
Cyber security monitoring is a test for any affiliation. Information Technology has transformed into an inherent and basic piece of business. Digitized information set away in the corporate IT base today, perhaps, never has an exclusion. Singular staff focal points, client records, pay rates, monetary parity unpretentious components, displaying and bargains information, advancement improvements, may all be secured in a database. Recollecting that cybercrimes are growing determinedly with extended innovation of attack, it has ended up being exceedingly fundamental for associations to counter these threats and infringement. As the hazard ends up being more amazing, realizing different layers of opposition ends up being dynamically basic.
Hazard organization so far was dreary and over the top. Most associations address the risks imperilling their IT systems with plans that make association overpowering and exorbitant. Anchoring the business servers takes firewalls and possible intrusion recognizable proof plans. These hindrances ought to have the ability to deal with the enthusiasm of steady applications. There are various point courses of action available today that handle security checking and IT-GRC issues uninhibitedly. Regardless, courses of action that engage end-to-end joining of front-line framework watching and IT-GRC have a greater intrigue. These game plans to ensure that the business has a bound together point of view of both operational security position and consistency organization. Consistency is to meet the real necessities; security is to meet your business requirements.
Associations that need to anchor their IT base from threats usually get a handle on the standard of protection all around. Regardless, it is basic to recollect the impact of your assurance all around framework while picking threat organization courses of action. Firewalls that turn away unapproved intrusions into private frameworks, and contamination scanners and confirmation suites that screen, and neutralize attacks are inadequate in solitude to anchor information. All of the stray pieces of an IT establishment needs to be guaranteed by a joining, enforceable security methodology.
In spite of the fact that cyber wrongdoing could conceivably be fiscally destroying to the normal individual, it is conceivable to cause disastrous repercussions by political fanatics that could abuse the Internet for demonstrations of cyber fear based oppression. What precisely is Cyber Terrorism? It is the point at which an individual or people utilize the secrecy and worldwide reach of the web for their very own increase, for example, psychological oppressor assaults on U.S. data framework in endeavours to seal cash, characters and arranged information. They can likewise utilize the web as an apparatus to discover similarly invested radicals to enable them to endeavour to hack their way into corporate or potentially government systems.
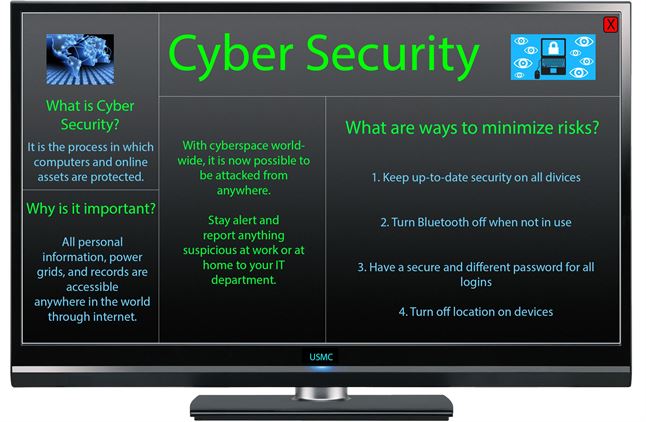
It is basic that the hazard organization course of action that is picked can pass on advanced relentless risk recognizable proof, data spillage, insider perils, malware examination, consistent controls affirmation, and framework e-exposure. It is in like manner fundamental to anchor email that demands to threaten to malware limits, as email is a standout amongst the most direct essential way contamination corrupts an IT structure. Thinking about adaptability, execution, and openness, anchoring the framework is pivotal. To feasibly counter the danger of information misuse, it is essential to have a plan of especially figured procedures and structures. Cyber security monitoring should be done regularly and taken seriously.
Pick an answer provider who can offer end-to-end motorization of all undertaking security, IT consistence, audit, and IT danger organization and pass on a broad response for security with straightforward and convincing security checking.

Lauren Richmond is a leading digital marketing expert at Traffic Plus, a dynamic firm dedicated to revolutionizing online presence for businesses of all sizes. With a deep passion for online growth and an expert grasp of cutting-edge marketing strategies, Lauren excels in crafting tailored solutions that drive meaningful website traffic.


1 thought on “Cyber Threat Monitoring Effectively”
Comments are closed.